Getty Pictures
Almost 71 million distinctive credentials stolen for logging into web sites comparable to Fb, Roblox, eBay, and Yahoo have been circulating on the Web for not less than 4 months, a researcher stated Wednesday.
Troy Hunt, operator of the Have I Been Pwned? breach notification service, stated the huge quantity of knowledge was posted to a widely known underground market that brokers gross sales of compromised credentials. Hunt stated he typically pays little consideration to dumps like these as a result of they merely compile and repackage beforehand printed passwords taken in earlier campaigns.
Not your typical password dump
Some obtrusive issues prevented Hunt from dismissing this one, particularly the contents indicating that almost 25 million of the credentials had by no means been leaked earlier than:
- 319 information totaling 104GB
- 70,840,771 distinctive electronic mail addresses
- 427,308 particular person HIBP subscribers impacted
- 65.03 p.c of addresses already in HIBP (based mostly on a 1,000 random pattern set)
“That final quantity was the true kicker,” Hunt wrote. “When a 3rd of the e-mail addresses have by no means been seen earlier than, that is statistically vital. This is not simply the standard assortment of repurposed lists wrapped up with a brand-new bow on it and handed off as the subsequent huge factor; it is a vital quantity of latest knowledge. Once you take a look at the above discussion board submit the info accompanied, the explanation why turns into clear: it is from ‘stealer logs’ or in different phrases, malware that has grabbed credentials from compromised machines.”
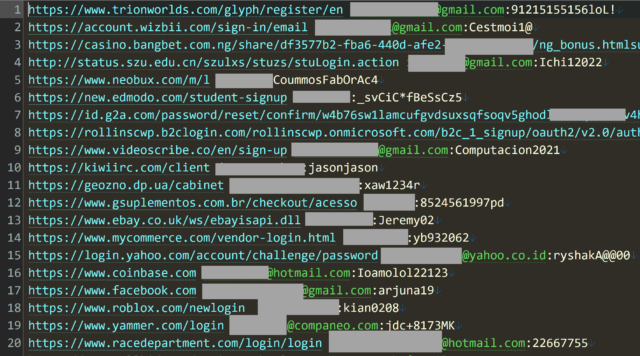
A redacted picture that Hunt posted displaying a small pattern of the uncovered credentials indicated that account credentials for a wide range of websites had been swept up. Websites included Fb, Roblox, Coinbase, Yammer, and Yahoo. In line with the declare that the credentials had been collected by a “stealer”—malware that runs on a sufferer’s system and uploads all person names and passwords entered right into a login web page—the passwords seem in plaintext. Account credentials taken in web site breaches are nearly all the time cryptographically hashed. (A tragic apart: A lot of the uncovered credentials are weak and would simply fall to a easy password dictionary assault.)
Have I Been Pwned?
Knowledge collected by Have I Been Pwned signifies this password weak spot runs rampant. Of the 100 million distinctive passwords amassed, they’ve appeared 1.3 billion occasions.
“To be truthful, there are situations of duplicated rows, however there’s additionally a large prevalence of individuals utilizing the identical password throughout a number of completely different providers and fully completely different folks utilizing the identical password (there are a finite set of canine names and years of delivery on the market…),” Hunt wrote. “And now greater than ever, the influence of this service is totally big!”
Hunt confirmed the authenticity of the dataset by contacting folks at a number of the listed emails. They confirmed that the credentials listed there have been—or not less than as soon as had been—correct. For added assurance, Hunt additionally checked a pattern of the credentials to see if the e-mail addresses had been related to accounts on the affected web sites. All of them did. A few of Hunt’s customers reported that the passwords gave the impression to be legitimate as of 2020 or 2021. Regardless of the date of the passwords, it stands to purpose that except they’ve been up to date, they continue to be legitimate. The underground market submit promoting the dataset stated it got here from a breach dubbed naz.api that had been donated to a special web site earlier.
Hunt stated that a big share of the credentials got here not from stealer malware as claimed, however from credential stuffing, a type of account-hijacking assault that collects giant numbers of stolen account credentials from earlier breaches. Hunt stated credential stuffing sources defined how a password he used “pre-2011” landed within the dump.
“A few of this knowledge doesn’t come from malware and has been round for a major time period,” he wrote. “My very own electronic mail handle, for instance, accompanied a password not used for properly over a decade and didn’t accompany a web site indicating it was sourced from malware.”
Making passwords protected
There are dozens of helpful primers on-line explaining how you can correctly safe accounts. The 2 essential substances to account safety are: (1) selecting sturdy passwords and (2) retaining them out of the sight of prying eyes. This implies:
- Creating a protracted, randomly generated password or passphrase. These passcodes ought to be not less than 11 characters for passwords and for passphrases not less than 4 phrases randomly chosen from a dictionary of no fewer than 50,000 entries. Bitwarden, a free, open supply password supervisor, is an efficient selection and a good way for much less skilled folks to get began. As soon as a password is created, it ought to be saved within the password-manager vault.
- Stopping sturdy passwords from being compromised. This entails not coming into passwords into phishing websites and retaining gadgets freed from malware.
- Use two-factor authentication, ideally with a safety key or authenticator app, at any time when potential. This doubly applies to defending the password supervisor with 2FA.
- Higher but, use passkeys, a brand new, industry-wide authentication commonplace that is resistant to theft by way of stealer apps and credential phishing.
It’s additionally a good suggestion to both create an account with Have I Been Pwned? or periodically enter electronic mail addresses into the positioning search field to examine if they seem in any breaches. To forestall abuse of the search, the positioning doesn’t log entered electronic mail addresses and no corresponding passwords are loaded with password knowledge saved on the positioning. Have I Been Pwned additionally accepts a single electronic mail handle at a time, besides in sure instances. You will discover extra on the service and the safety of utilizing it right here.
Have I Been Pwned additionally permits customers to go looking its database for particular passwords. Extra about k-anonymity and different measures Hunt makes use of to forestall password publicity and abuse of his service is right here.
This submit has been up to date to appropriate inferences about how Hunt’s password ended up within the dataset.




