Within the first a part of this trilogy, we talked about 10 commonest methods India’s cybercriminals goal us whereas right here Satyen Okay. Bordoloi expands the crimeverse with 15 extra methods wherein they will cheat you and within the subsequent half, how one can arm your self in opposition to them.
Final September, when Assam Police Crime Department obtained a tip-off a few pretend name centre in Guwahati, they believed it to be a routine job. However what Guwahati Police ended up unearthing, was a multi-crore rip-off that had eight unlawful name centres to rip-off each Indians and foreigners within the guise of providing technical help. These ‘name centres’ have been working for 2 years with staff from throughout India. Three masterminds have been arrested and almost 200 ’staff’ have been detained.
Within the earlier half, we highlighted the ten commonest methods cybercriminals goal us as highlighted by the Indian Cybercrime Coordination Centre (I4C). On this half, we are going to increase the crimeverse to let you know of 15 extra methods in which you’ll fall prey to scammers and lose your treasured cash and peace of thoughts.
FAKE TECH SUPPORT SCAM:
If one coordinated raid in far-off Guwahati can unearth 8 name centres producing crores each month, you may think about the extent this rip-off is prospering throughout India. Certainly, in the previous couple of years, police throughout the nation have made quite a few arrests the place cybercriminals ran pretend tech help. The best way it really works is easy: a pop-up if you go to some web site would lure you to them, or they’d contact immediately claiming to be from a well known firm or group like a financial institution, a tech help firm, authorities company and so on. They declare your checking account has been compromised, your laptop has a virus, or your social media account has been hacked and so on. They don’t ask for cash however will ask you to put in distant desktop software program in your ‘contaminated’ system to treatment it. Later, they’d steal your cash by having access to your financial institution accounts, passwords and so on. by planting malware.

ONLINE QUIZZES AND SURVEYS:
Quizzes or surveys on websites could appear innocent. However these can be utilized to gather your private data, which might result in id theft and social engineering scams the place scammers impersonate individuals near you to steal cash or information. Watch out in regards to the data you give out in such surveys, and ideally fill them up provided that they’re from completely dependable sources.
PUBLIC Wi-Fi TRAPS:
Free Wi-Fi at public locations like prepare, bus or aircraft stations is all the time attractive. However these may be traps intentionally arrange by cybercriminals. As soon as you utilize their community, something you ship to them might be intercepted by them. In making an attempt to avoid wasting just a few rupees, you would lose rather more in such unsecured public Wi-Fi networks
PIGGYBACKING AND SHOULDER SURFING:
Just a few weeks in the past, Wall Avenue Journal did an excellent collection together with a podcast about how criminals steal telephones at public locations. Whenever you use a password to open your cellphone in public, somebody round may be watching you enter it. In the event that they steal your cellphone left on the bar or desk later, they will open it with the password they noticed over your shoulders. The WSJ collection highlighted how by doing this they cannot solely steal cash, however lock you out of all of your information, together with pictures and wipe them clear, in essence erasing your recollections, and hack your social media and different accounts as effectively.
RANSOMWARE:
Final 12 months AIIMS, Delhi was locked out of their very own laptop methods after ransomware debilitated them. The attackers requested for cash to revive it. Although, normally, ransomware peddlers goal large corporations or establishments, people aren’t secure both and as we highlighted in a earlier article on Sify, we should be cautious.
PYRAMID SCHEMES / INVESTMENT SCAMS / CRYPTO SCAMS:
Sure, the old-world pyramid schemes of the bodily world, have a digital avatar. The rip-off is commonly easy: ‘make investments’ cash for a set interval through an app that guarantees to double it – typically it’s through cryptocurrency, encourage others to do the identical and get wealthy. A relative in Assam misplaced over a lakh to this rip-off the place they doubled their small preliminary funding inside months, however as soon as they and others they impressed had invested extra, the app and firm disappeared. These scammers typically use the mumbo-jumbo of cryptocurrency. Watch out for such pretend investments, pump-and-dump, pyramid and/or crypto scams, Ponzi schemes, and fraudulent exchanges that promise you a doubling of your cash in a short while.

DATING SCAMS – LOCAL AND INTERNATIONAL:
This has many variants. Ladies lure wealthy males on relationship or marriage portals, construct a relationship – typically sexual – to realize belief and later blackmail individuals. The male model works on matrimonial websites the place a person pretends to be a wealthy man or a high-profile authorities servant however disappears earlier than or after marriage after extracting cash from the lady or her household. The worldwide model is when an NRI pretends to have a high-paying job abroad, marries and takes dowry and both by no means takes the woman overseas, or takes her and both dumps her or makes use of her like a slave. A smaller model of this rip-off is when a lady calls a person matched on a relationship app for a date in a pre-fixed restaurant and has dinner and drinks that ought to have value just a few thousand, however value him ten or fifteen occasions extra.
FAKE JOB OFFERS:
One other pal misplaced almost a lakh to scammers who contacted him through legitimate-looking emails to get him a job in Canada. The job wasn’t there, and the boys disappeared as soon as they’d his cash. Luring victims with interesting job provides whether or not in the identical nation or overseas to steal private data or cash has develop into a profitable methodology utilized by cybercriminals to take advantage of the vulnerabilities of individuals.

STEALING CREDIT/DEBIT CARD DATA:
The man on the counter gave me the POS card terminal for me to enter my password for cost. I did whereas hiding the keypad. He took the terminal, checked out it and mentioned sorry, I had forgotten to enter the quantity. What that particular person had achieved, was very neatly work out tips on how to know my four-digit debit card passcode. That, together with skimming my card which he may have achieved since I handed him the cardboard inside his cabin and wasn’t paying sufficient consideration, he now had entry to my card information which he may have used for something, besides, I modified my pin as soon as once more as a result of I noticed this. This was a classy operation, however normally, it’s achieved utilizing a compromised cost terminal or through phishing.
‘BOSS SCAM’ OR BUSINESS EMAIL COMPROMISE (BEC):
The COVID pandemic made do business from home a necessity. As we labored away from each other, the BEC or ‘Boss Rip-off’, emerged. This can be a sort of cyber-attack the place fraudsters impersonate high executives of an organization, and feign a piece emergency to stress an worker into performing rapidly to both switch cash or share information that can be utilized to compromise later. You may learn an instance of this at first of the subsequent a part of this collection.
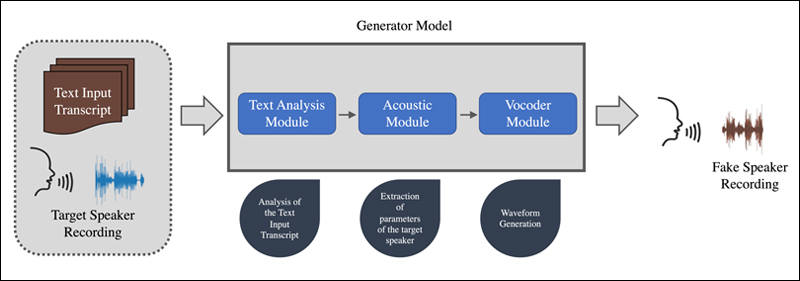
VOICE AND VIDEO DEEPFAKES:
You get a name from a lawyer saying your son, daughter or grandchild is in bother as they’ve been arrested. They provide the cellphone to this relative in bother and certain sufficient, you hear their panicked voice and know it’s them, so that you do what the ‘lawyer’ tells you and switch cash. It’s only later, that you simply realise that you’ve been scammed because the mentioned relative in query had all the time been secure. These are new sorts of scams the place utilizing just some second pattern of somebody’s sound, AI can be utilized to copy them and idiot individuals on this means.
MOBILE APP THREATS:
The rationale why each Apple with their App Retailer and Google’s Play Retailer are so explicit that you simply obtain apps solely from their shops, is as a result of they test the apps posted there. But, sometimes some do slip by and these malicious apps or adware on cell gadgets can steal information, observe location, or spy in your actions. Downloading and utilizing apps from exterior these official app shops is extraordinarily dangerous.
(Picture Created on Bing.com)
INTERNET OF THINGS (IoT) EXPLOITATION:
You may swap on the AC of your house out of your cell system whilst you’re nonetheless on the best way, or change the color of your electrical bulb. Life has develop into simple and enjoyable due to IoT gadgets related to the community. Nonetheless, these gadgets can develop into one other means by which hackers can acquire entry to both your private data or disrupt networks.
ZERO-DAY ATTACKS:
Together with Phishing, this is likely one of the oldest methods of wounding a digital person. Each program or system we set up on our digital gadgets may have beforehand unknown vulnerabilities of their software program. Typically our methods themselves would have such vulnerabilities we had no concept about. Hackers are on the fixed lookout to take advantage of them earlier than builders can patch them up.

(Picture Created on Bing.com)
SOCIAL ENGINEERING:
Not all cybercriminals use risk or urgency to rip-off you. The actually good one includes social engineering. Many have been cheated by somebody they met on-line, bought right into a relationship of belief just for the particular person to ask for cash and disappear. At occasions, individuals declare to be an previous pal from faculty, reminding you of the great occasions you had. The info match so that you belief the particular person and once more, after months of such correspondence – normally it’s by no means an actual assembly – they ask you for cash to tide over an emergency, you belief and provides, after which the particular person disappears, and also you realise the pal this fraudster has been impersonating, has been lifeless years. The suave cybercriminals get a kick out of exploiting human feelings and belief, to govern victims into making errors or handing over data by intelligent storytelling, emotional appeals, or pretend authority figures. However the place did they get this data to cheat you: your social media accounts.
These are 25 of the most typical methods in which you’ll be baited, hooked and caught in an internet of digital scams the place you cannot solely lose cash however recollections and peace of thoughts. However life needn’t be this troublesome. There are some easy methods in which you’ll hold your self and your loved ones secure. Some you’d have discovered by the very means wherein the criminals attempt to cheat you. Within the subsequent a part of this trilogy, we take an in depth look into how one can defend your self with good digital hygiene, in a world awash with digital viruses and cybercriminals.




